-
For Hair Color Changer • Vehicle Counter • Smart CCTV Detection
Purpose-Built AI Vision Solutions
Purpose-built AI vision systems engineered to deliver precise, real-time visual intelligence across beauty, traffic analytics, and smart security applications. -
24/7 Smart Monitoring
Precision Detection & Continuous Tracking
AI-powered , vision to detect and track what matters most -
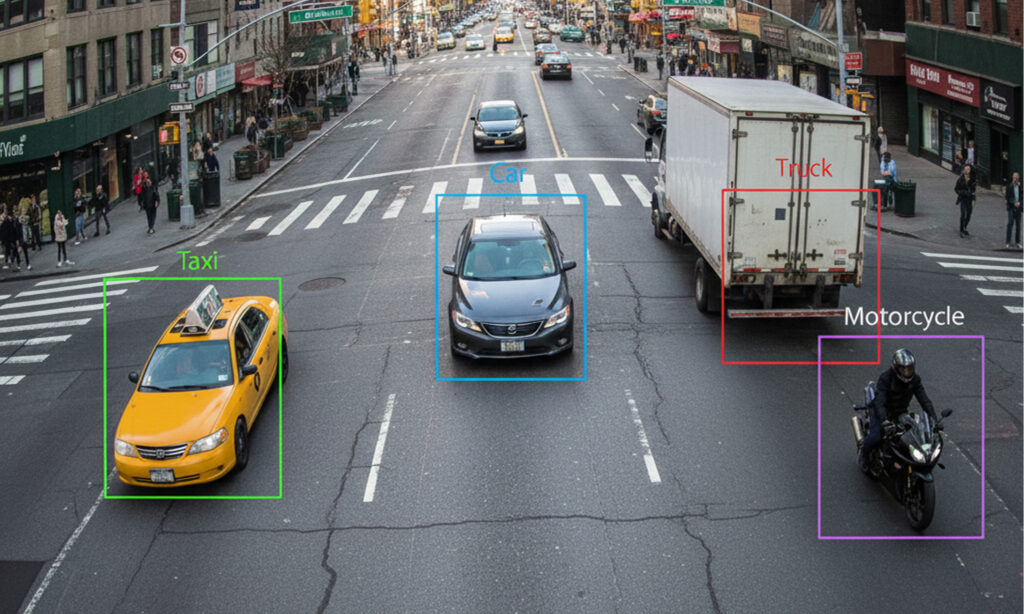
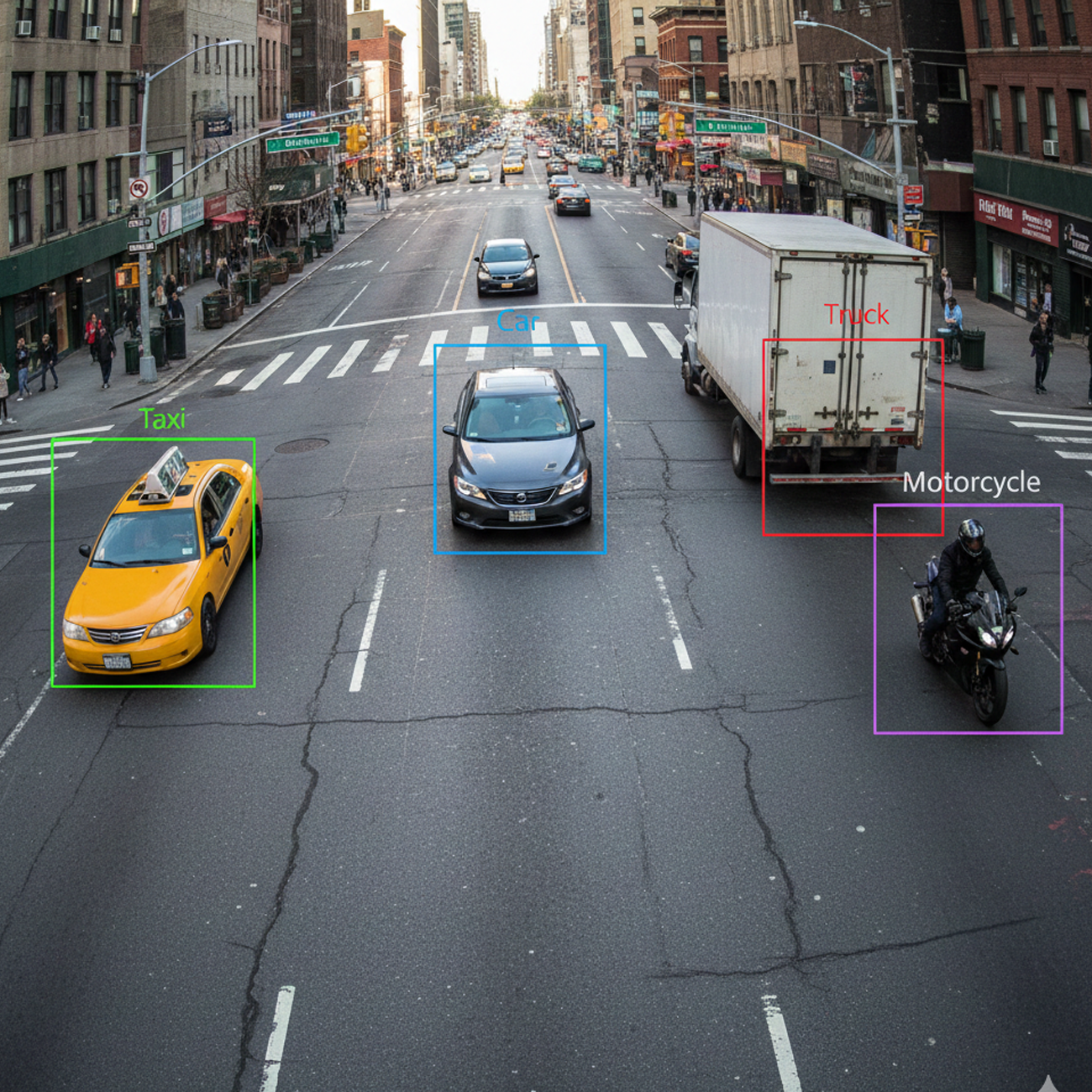
Advanced AI-Powered Traffic Intelligence
Traffic Analysis
Advanced AI simultaneously counts pedestrians and all vehicle types, providing comprehensive intersection intelligence in a unified system for precise traffic analysis and urban planning. -
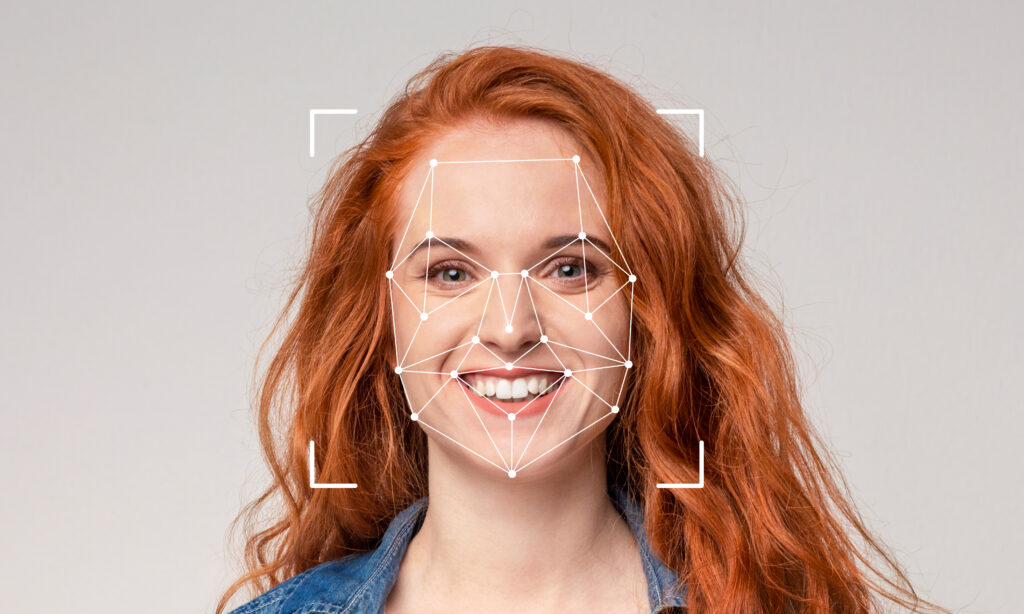
Real-Time AI Beauty Transformation
Secure Real-Time AI Beauty
Our AI-powered beauty engine performs real-time facial analysis and pixel-level segmentation to apply hyper-realistic hair and makeup transformations with natural lighting and texture preservation. All processing runs securely on-device with zero latency, delivering instant, lifelike results without uploads or filters. -
Flexible Security Built for Your Specific Challenges
Smart AI Solutions Designed for Every Environment
Across factories, cities, and secure facilities , our system is tailored to your operational demands. -
Instant Alerts in Critical Moments
Real-time Video Processing
Our system detects and reports threats and important events in minimum time
-
Complete Support & Continuous Updates
Development Based on Customer Requests
Our technical team is always ready to add new features to your system
Protection Plans
Our Services, Your Peace of Mind
- Healthcare Pro
- Retail Analytics Pro
- Industrial SafeGuard
- Hotel Security
- Smart Correctional Monitoring System
- Banking Shield
- Airport Command
- Education Guardian
- Heritage Guard
- Urban Smart City Platform
- Energy Secure
- Port Master
- Transit Control
- Urban Emergency Management System
Assessment and Analysis
Strategy Development
Ongoing Improvement
SEE OUR DEMO
Cut Security Costs by 60-80% • Advanced AI Video Analytics • Real-time Threat Detection • 24/7 Smart Monitoring • Reduce Guard Requirements by Half
Cut Security Costs by 60-80% • Advanced AI Video Analytics • Real-time Threat Detection • 24/7 Smart Monitoring • Reduce Guard Requirements by Half
ROI in Just 6 Months • Save $50K+ Annually on Security • One System Replaces Multiple Guards • AI That Never Sleeps or Takes Breaks • Future-Proof Security Technology
ROI in Just 6 Months • Save $50K+ Annually on Security • One System Replaces Multiple Guards • AI That Never Sleeps or Takes Breaks • Future-Proof Security Technology
Watch Multiple Locations from One Screen • Zoom into Any Incident Instantly • Track Objects Across Camera Networks • Remember Every Face, Every Event • Your All-Seeing Digital Eye
Watch Multiple Locations from One Screen • Zoom into Any Incident Instantly • Track Objects Across Camera Networks • Remember Every Face, Every Event • Your All-Seeing Digital Eye
SeeDeep Overview
Beyond Security, Inside the World of Computer Vision

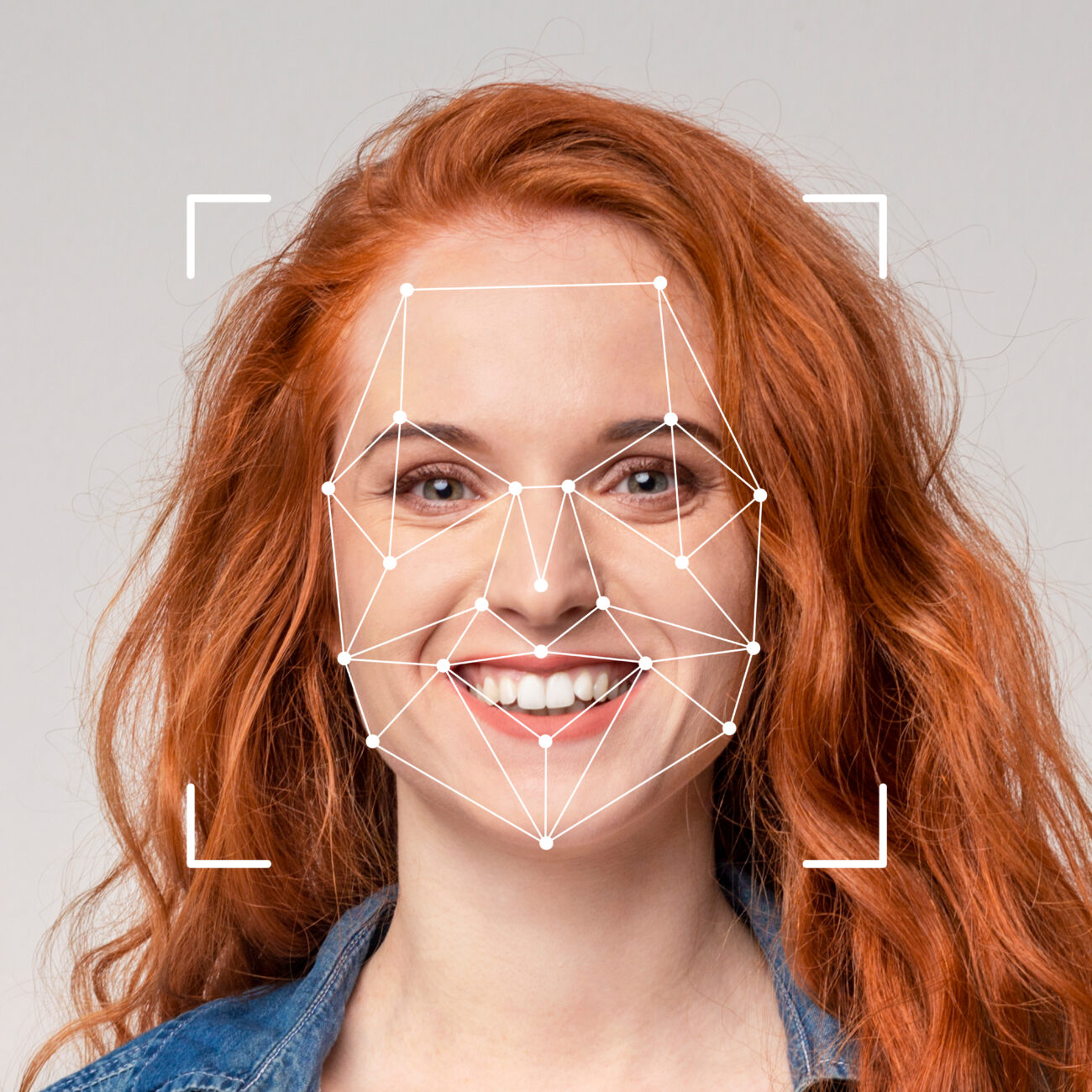

Risk Reduction
Incident Prevention
Data Protection
At SeeDeep, we leverage advanced instance segmentation and deep learning–based color mapping to enable intelligent, pixel-accurate hair color transformation while fully preserving natural texture, lighting, and shading; the system performs in real time with no quality degradation, delivering highly realistic simulation for beauty and digital applications.”
At SeeDeep, we utilize real-time object detection and instance segmentation to accurately identify vehicles and pedestrians, while motion vector analysis determines traffic directions, flow patterns, and congestion formation across multi-camera environments.
At SeeDeep, we unify CCTV networks into a single intelligent vision system for real-time object and human detection, trajectory tracking, and automated abnormal behavior analysis.
1.
Identification of Assets
The first step is to identify what needs protection. This includes physical assets like buildings, equipment, and inventory, as well as digital assets like data, networks, and software, and human assets such as employees or VIPs.
2.
Threat Assessment
Evaluate potential threats that could harm the identified assets. Threats can be natural (e.g., earthquakes, floods), human (e.g., theft, cyberattacks), or environmental (e.g., fires, chemical spills).
3.
Vulnerability Assessment
Determine the weaknesses or vulnerabilities in the security of the assets. This involves assessing how susceptible each asset is to the identified threats.
4.
Risk Analysis
Calculate the level of risk by combining the likelihood of a threat occurring with the potential impact it would have on the asset. This helps prioritize security measures.
About Security
Your Source for Safety News
Meet Our Staff
United for Your Safety
AI Hair Color Changer: Real-Time, Hyper-Realistic Beauty Transformation with SeeDeep
Choosing a hair color has always been a high-stakes decision. Once applied, the result stays with you — sometimes longer than expected. AI-powered Hair Color Changer technology b
AI-Powered Intelligent Surveillance Cost Optimization
Security has always been a critical pillar of industrial operations, but in recent years, the cost of maintaining large surveillance infrastructures has increased faster than most
High-Precision Object & Human Tracking in Low-Light & Crowded Areas
High-Precision Object & Human Tracking has become one of the most critical capabilities in modern AI-driven surveillance. As environments grow denser and lighting conditions be
AI-Powered Smart Surveillance | Intelligent Security by SeeDeep
AI-powered smart surveillance is no longer a futuristic concept—it has become an operational necessity for modern organizations. As security threats evolve faster than human resp
Multi-Camera Integration by SeeDeep.ai | Unifying Surveillance Into One Intelligent System
Modern industrial and corporate environments rely heavily on video surveillance.But adding more cameras does not automatically improve security.In fact, more cameras often create m
Real-Time Threat Detection : How SeeDeep.ai Predicts and Prevents Incidents Before They Happen
Real-time threat detection has become a critical necessity for modern facilities, not just an advanced security feature. In environments where incidents can escalate within seconds
How SeeDeep.ai Uses AI to Deliver Smarter, Continuous Protection Than Traditional Security Guards
For decades, facility security depended almost entirely on human guards — people scanning monitors, walking through hallways, and reacting to potential risks. But as environments
The All-Seeing Eye — How SeeDeep.ai Understands Buildings, Networks & Human Movement
Traditional CCTV systems were built to “capture” moments — not understand them. They record thousands of hours of footage, but offer almost zero intelligence unless a human m
Cutting Security Costs by Up to 60% — The Real Power Behind SeeDeep.ai
Security has become one of the most expensive operational components for modern industries. Companies face mounting costs: expanding surveillance infrastructure, hiring more staff,